Is Decentralized Cloud Storage the Next Big Web3 Industry?
Why we need decentralized cloud storage, how it works, and popular dStorage protocols & platforms like IPFS, Swarm, Filecoin, etc.
No time to read? Learn all about sports NFTs through your favorite podcast platform 👇
GM DOers!
In recent years, the world has witnessed tremendous growth in the amount of data being generated, stored, and accessed every day.
With this explosion of data comes the need for more efficient and secure storage solutions.
Decentralized storage is a promising technology that has emerged to address the limitations of traditional centralized storage systems like: AWS, iCloud and Dropbox.
Unlike centralized storage, which relies on a single entity to manage data, decentralized storage leverages a network of computers to store data in a distributed manner.
This approach offers several advantages, including improved security, privacy, and resilience.
Today we have CryptoShuriken, founder of the CryptoShuriken Blog sharing his knowledge on the subject.
He’ll be covering:
- What decentralized storage is.
- The need for decentralized storage.
- How decentralized storage works.
- Decentralized storage protocols and platforms.
Now, let’s go!
👉 Brought to You by Lens: The Future of Social Networking 👀
So, What is Decentralized Storage?
As its name implies, Decentralized storage is a type of storage system that does not rely on a central server or authority.
Unlike a centralized storage system which is managed & operated by a single centralized entity, decentralized storage is operated by a peer-to-peer network of user-operated nodes, each of which stores a copy of the data creating a resilient file storage-sharing system.
This makes it much more resistant to censorship and attack than traditional storage systems.
Aka, it prevents disasters like these 👇 from happening.

The Need for Decentralized Storage
In modern days, cloud services, such as Google Drive, AWS, and Dropbox, have been the go-to option for hosting files and websites.
While these services have helped individuals, startups, and large companies relieve the hassle of managing their own storage infrastructure, the centralized nature of such services present some deep flaws.
One of the many flaws of centralized storage services is that they are easy to censor. If a government or other authority does not want certain information to be out there, they can simply order the centralized storage providers to remove it and not store it in the future.
Furthermore, they can even make changes to the contents of the data stored, resulting in poor information integrity.
Another flaw is that centralized storage services are vulnerable to attack. If hackers can gain access to the servers of a centralized storage provider, they can potentially access and even delete all of the data that is stored on those servers.
Since these services have data hosted on centralized servers, having a single point of failure means any outage can result in temporary, or even permanent loss of data.
Decentralized Storage provides a solution to all these problems by providing a censorship-resistant, secure, distributed, efficient, robust, cost-effective, and resilient form of data storage.
How does Decentralized Storage Work?
The Decentralized Storage model works by distributing a copy or a portion of the entire data across a peer-to-peer network of nodes, each of which is incentivized to store the data.
By storing data redundantly across multiple nodes, the decentralized storage system ensures data security and accessibility. When the same piece of data is stored across multiple nodes (even if a couple of nodes go down) the data can still be retrieved from the rest of the storage nodes.

What’s in it for the Node Operators?
We all have unused space available in our computer and mobile device storage. The decentralized storage system makes use of available storage space on the node operator’s disk drives, and node operators are incentivized to rent out unused storage space on their devices to the decentralized storage networks.
Now, let’s learn about different decentralized storage protocols & platforms, and their inner workings.
But before that, let us tell you about the tool we use to bring our PRO members on-chain. 👀👇
🤝 Together with Kazm: The All-In-One Tool for Building a Thriving Web3 Community
Are you building a community in web3? Then you need Kazm, the tool we use to onboard our members a
Community is central to everything we do in web3, but only if you truly understand your members…
That’s where Kazm comes in.
It’s the must-have web3 tool for onboarding and managing your members that combines both on-chain and web2 metrics in one place.
- Want to provide a customized and gated onboarding experience? ✅
- Attribution tracking so you know exactly which campaigns are driving ROI? ✅
- On- and off-chain automations and integrations so you can focus on the big picture? ✅
Your community is already on-chain, get to know them better with Kazm today.
Decentralized Storage Protocols and Platforms
For starters, we can even consider the Ethereum blockchain itself to be a decentralized storage system, and to some extent, it is, for code (smart contracts) storage.
But when it comes to storing large amounts of data (those JPEGs, gifs, and massive MP4s), it becomes a bit unfeasible, not to mention gas-inefficient, since this isn’t what it was originally designed for.
So, we need to look at other solutions that are tailor-made for storage purposes.
Solution #1: IPFS
IPFS is a peer-to-peer protocol for storing, accessing, and sharing data in a distributed file system.
What does that mumbo jumbo even mean? Let’s look at an example:
We all love Twitter (the little bird app is so cool). To access Twitter, you put in the “https://twitter.com” URL in your browser, and since it points to Twitter’s IP address, we get what webpage the server on that address stores.
But if we put Twitter on IPFS, we don’t get an IP address. Instead, we get a content identifier, or CID, to access Twitter that looks something like this:
/ipfs/QmfExSLtVQwsFJNcN6AaW8DZsrL9CYsbHmxVdeLWkRzuyjInstead of finding data by its location, IPFS finds it by its contents.
How does IPFS work?
Right now, there’s a problem that exists on the internet; that content is found by its location. You wanna Netflix and chill? Cool, go to”netflix.com”. You wanna read CryptoShuriken’s blog? Visit “cryptoshuiken.com. But what if the location of the content changes for some reason? 🤔
Content addressing fixes this problem. By content addressing, every piece of content has a CID, which is based on the data’s cryptographic hash, that points to data in IPFS.
That means two exactly similar files will have the same CID. Any minute difference in the content will generate a completely different CID. IPFS uses the SHA256 hashing algorithm by default to generate CIDs.
IPFS uses content addressing to identify and find content, rather than looking at where it’s located.
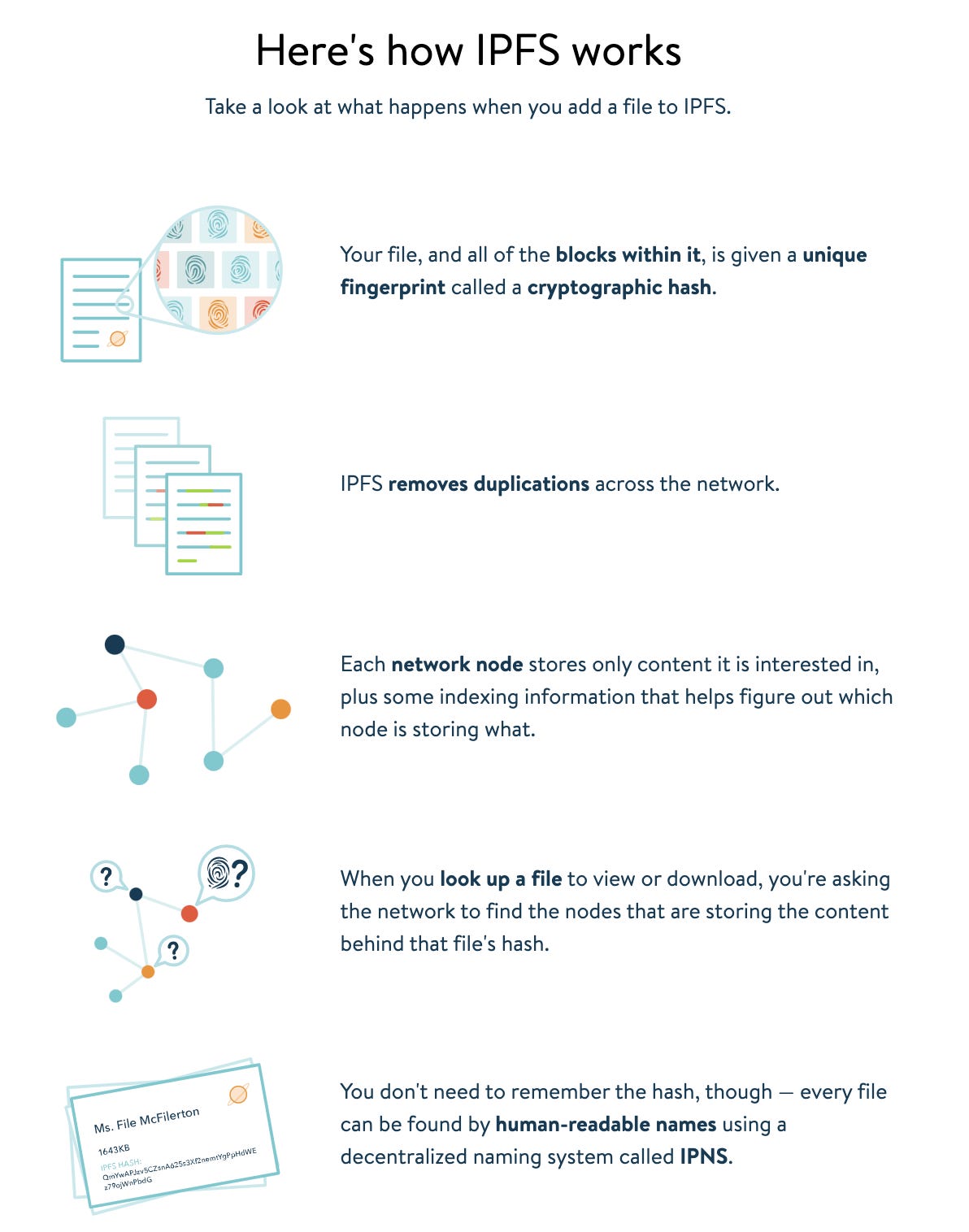
There’s so much to these dStorage protocols that each of them deserves a detailed blog post. For ex, IPFS uses Merkle DAGs for representing files and directories. We’ll stick to just the basics in this blog post for now.
Solution #2: Filecoin
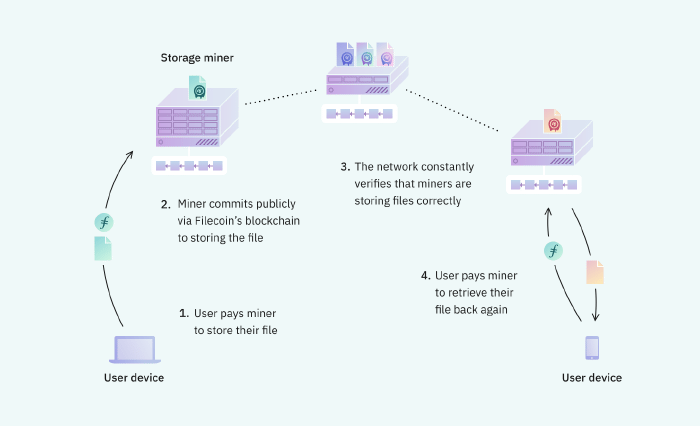
Filecoin is a peer-to-peer network built on top of IPFS, created by the same team behind IPFS, that incentivizes users to rent out unused storage space by rewarding Filecoin’s native ‘FIL’ token.
In Filecoin, users pay for storage space, and anyone who wants to store other users’ files can join the Filecoin network, and get paid.
Solution #3: Swarm
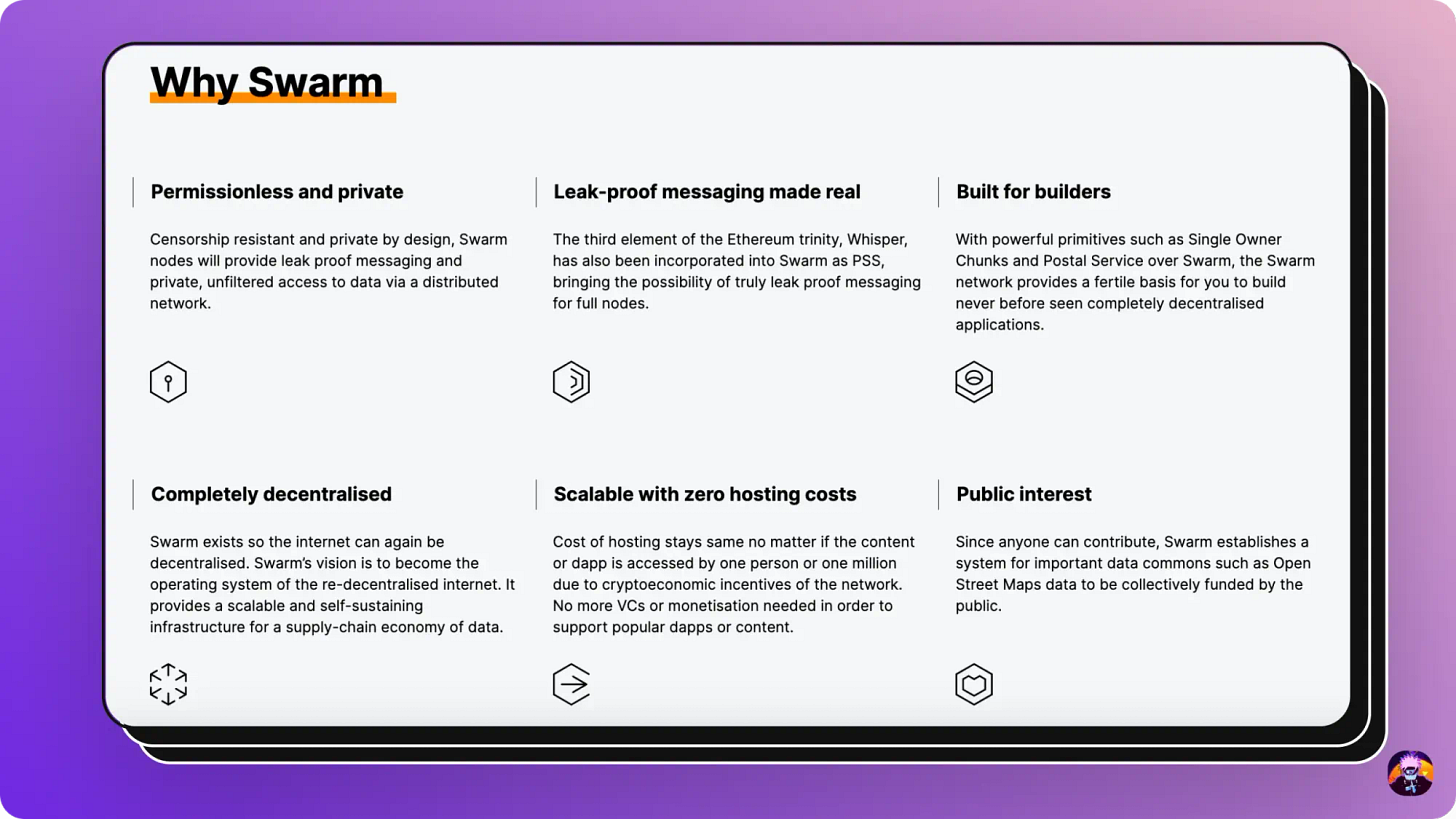
Swarm is another decentralized storage protocol that is a part of Ethereum’s Holy Trinity: Ethereum for computing power, Whisper for messaging, and Swarm for storage.
Swarm provides a completely decentralized storage infrastructure that allows people from all over the world to become storage providers and get paid while doing so.
Swarm is designed to be highly scalable and resilient, and to provide a platform for applications that require a high degree of security and censorship resistance.
The idea for Swarm was presented by Gavin Wood and its development is mainly funded by the Ethereum Foundation.
Difference between IPFS & Swarm
While both protocols may look similar from a high level, there are subtle differences that exist when we dive deeper into the inner workings and philosophies behind these protocols.
Some of them are:
- Swarm’s core storage component uses an immutable content-addressed chunk store while IPFS uses distributed hash tables to find which peers are hosting the content. (A hash table is a database of keys to values. A distributed hash table is one where the table is split across all the peers in a distributed network.)
- Since Swarm is a part of the Ethereum Holy Trinity, it has deep integration with the Ethereum blockchain for the incentive system, whereas IPFS has no incentive system of its own and utilizes Filecoin to add an incentivization layer.
- From a development standpoint, IPFS is much further along in code maturity, adoption, and community engagement as compared to Swarm. As a result, IPFS has a lot of content available in terms of documentation, whereas Swarm doesn’t have a large documentation base (heck, even the info I found while researching about Swarm was from third-party blogs 😞).
There are a lot of similarities and differences between both these protocols. For more details, check out this wiki (although a bit dated).
Go PRO and get weekly on-chain analysis combined with industry insights to understand how to build and invest in web3
Solution #4: Arweave
Arweave is a decentralized storage platform that uses a new type of data structure called a blockweave. Blockweaves allow Arweave to offer scalable, resilient, and efficient storage.
So, what are Blockweaves? 🤔
Blockweave is the core technology behind Arweave.
We all know that a blockchain is just a chain of linked blocks that contains transaction data. Blockweaves are similar to blockchain in that they are a chain of blocks, but it contains storage data, linking to multiple previous blocks from the network
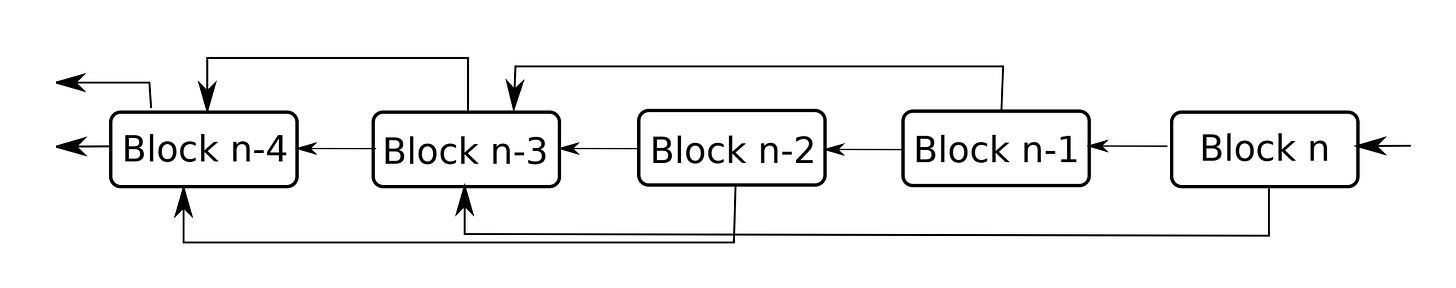
Blockweaves work by enforcing that the miners provide a ‘Proof-of-Access’ to old data in order to add new blocks.
Unlike a more traditional blockchain, where miners spend compute power and electricity and compete to mine a block in order to earn tokens, the Arweave network encourages miners to store & replicate valuable data in order to earn tokens.
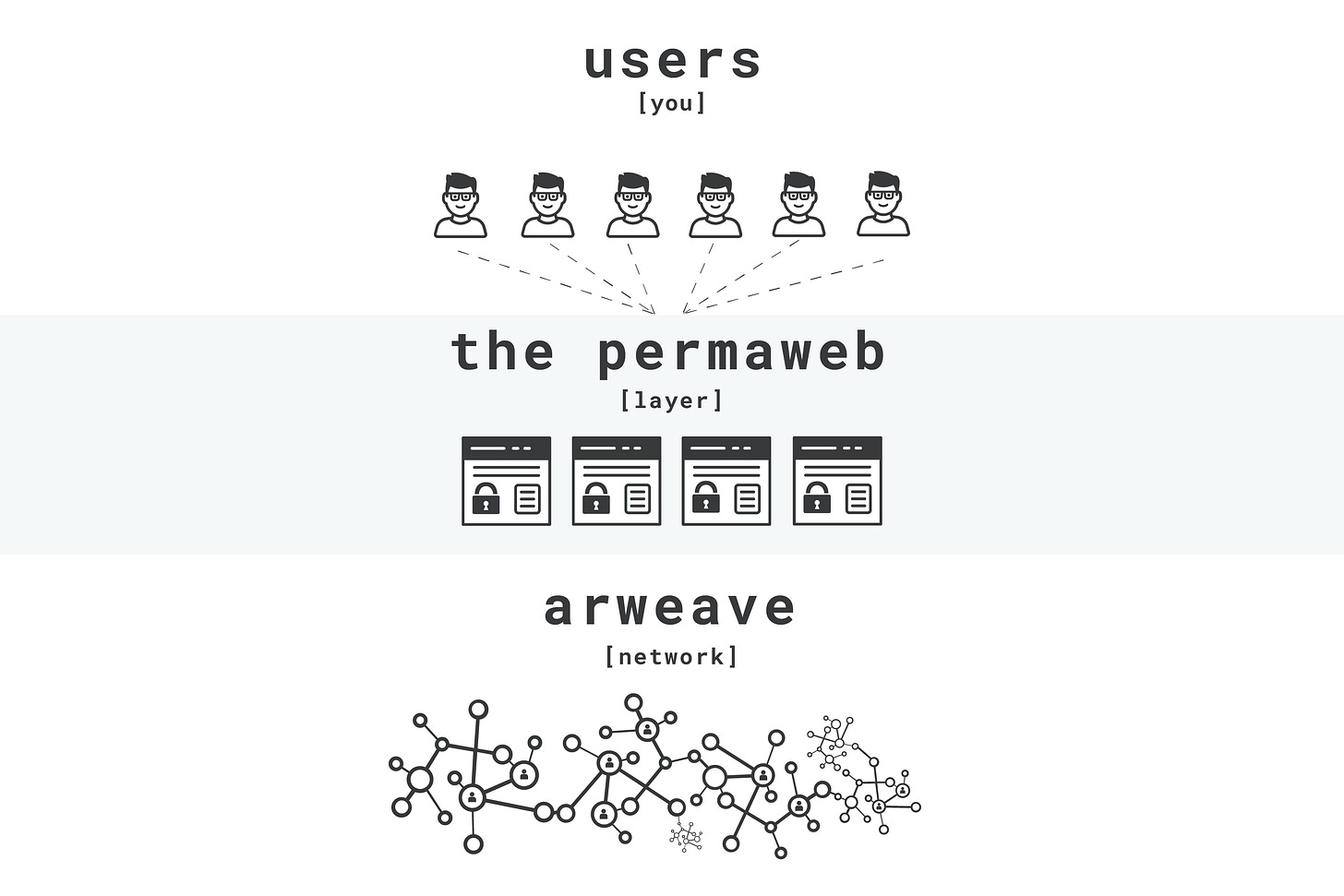
The Permaweb
The Permaweb, just like the traditional web, is a collection of interlinked documents and applications that are stored permanently. The Permaweb sits on top of the Arweave data storage layer.
Since the Arweave network is built on HTTP, just like the traditional web, web browsers have access to the data stored in the network.
Solution #5: Storj
Storj is a decentralized storage platform that provides secure, scalable, private, efficient, and S3-compatible decentralized cloud object storage.
Similar to other decentralized storage platforms, Storj connects people with unused bandwidth and storage space to those who need cheap, accessible, and private file storage.
Storj uses ‘STORJ’, their native ERC-20 token, to incentivize people who are renting out bandwidth & storage space.
Solution #6: SIA
Sia is another popular decentralized cloud storage platform that connects renters (who rent out storage space to host their files & applications) and hosts (who lend their storage space to renters) together in a peer-to-peer network. Sia has its own blockchain and the hosts get rewarded with Sia’s own native utility token ‘SiaCoin’.
Once the renter uploads their file to the Sia network, it gets split up, encrypted, and sent all over the world. The network ensures the files are always accessible by making multiple copies of them.
And since the files are split up into multiple pieces & encrypted, they are inaccessible to the hosts.

SOCIALS
Meme of the Week
Conclusion
With the mainstream adoption of centralized storage networks in the past decade and with centralized cloud services, like Google & AWS, providing a fast & cheap storage infrastructure to individuals and organizations, threats of poor information integrity, privacy, and censorship have been omnipresent.
The decentralized storage model addresses the issue of centralized storage by distributing the data across a network of distributed nodes, each of which stores a copy of the data.
This makes it much more resistant to censorship & attacks with better information integrity and data availability than traditional storage systems.
ABOUT THE AUTHOR
- CryptoShuriken
- Founder of CryptoShuriken’s Blog – Writing engaging content on all things Web3.
- Find him: Twitter

FOR THE DOERS
Take Action & Level Up
LEARN
Take our FREE Web3 Rabbit Hole Course to get up-to-speed on the foundational components of Web3 so you can confidently build, work, or use the fastest growing technology in history.
APPLY
Think you’ve got the writing skills and passion to create content for Web3 Academy? Then check out the role we have open: Web3 Content Writer?.
VERIFY
Is Ethereum in the middle of an on-chain bull run during this bear market? The numbers don’t lie: Is Ethereum Scaling?